Juniper Security Associate (JNCIA-SEC) You can demonstrate a deep understanding of security technologies in general as well as Junos OS software for SRX Series devices in the Security track. For networking professionals with beginner-intermediate knowledge of the Juniper Networks Junos OS for SRX Series devices, the associate-level certification in this course is JNCIA-SEC. Your knowledge of security technologies, together with ...
Read More »Author Archives: firewalltraining
Juniper Design Training
Juniper Design Training COURSE LEVEL Introductory-level course AUDIENCE This course is intended for students who are proficient in operation and configuration and who want to expand their skill sets by learning the fundamentals of network architecture. PREREQUISITES Knowledge of routing and switching architectures and protocols. Knowledge of Juniper Networks products and solutions. Understanding of infrastructure security principles. Basic knowledge of ...
Read More »Juniper Mist Training
Juniper Mist Training The suggested preparation for the Mist, Associate (JNCIA-Mist AI) certification is this Mist Masters self-paced, on-demand course (‘Mist Wi-Fi Certification’). WLAN fundamentals, design considerations, wired assurance, and deployment and migration options are all introduced in this course. It addresses WLAN monitoring, Mist AI setups, and topics like location services and service-level expectations (SLEs). Cost: $0.00 USD This ...
Read More »Juniper Automation and DevOps
Juniper Automation and DevOps You can demonstrate proficiency in popular scripting languages and technologies for automating device and network tasks by earning a certification in automation and devops. The associate-level certification in this course, the JNCIA-DevOps, is meant for networking professionals who have a basic understanding of automation technologies and best practises. Your knowledge of DevOps and automation concepts as ...
Read More »Juniper Cloud Training
Juniper Cloud Training You can demonstrate your proficiency with cloud networking architectures like multiclouds, software-defined networking, SD-WAN, and other cloud technologies using the cloud track. For networking professionals with introductory-level understanding of Juniper Networks cloud-based networking topologies, theory, and best practises, there is the associate-level certification JNCIA-Cloud. Your knowledge of cloud-based networking principles and technologies is validated by the written ...
Read More »Juniper Data Center Training
Juniper Data Center Training You can demonstrate your proficiency with cutting-edge data centre technologies, as well as related configuration and troubleshooting abilities, by choosing the Data Center route. The professional-level certification in this course, the JNCIP-DC, is created for data centre networking experts who have in-depth knowledge of Juniper Networks’ Junos software and hardware. Your knowledge of data centre technologies, ...
Read More »Juniper Enterprise Routing and Switching Training
Juniper Enterprise Routing and Switching Training INTRODUCTION TO THE JUNOS OPERATING SYSTEM (IJOS) Junos device families and discusses the key architectural components of the software. Key topics include user interface options with a heavy focus on the command-line interface (CLI). Students who complete this three-day course will be equipped with the fundamental skills needed to operate the Junos operating system ...
Read More »Juniper Service Provider Routing and Switching Training
Juniper Service Provider Routing and Switching Training You can demonstrate your familiarity with Juniper Networks’ enterprise routing and switching platforms as well as networking technology in general on this route. For seasoned networking workers with basic to intermediate knowledge of routing and switching implementations in Junos, the specialist-level certification in this track, JNCIS-ENT, is created. Your knowledge of fundamental routing ...
Read More »Juniper Firewall Training
Juniper Firewall Training Juniper Networks Certification Tracks Leverage Juniper’s certification tracks to determine the recommended order in which courses should be taken based on your preferred area of concentration and certification goals. Juniper Networks Certification Tracks Security, Associate (JNCIA-SEC) Security, Specialist (JNCIS-SEC) Security, Professional (JNCIP-SEC) Security, Expert (JNCIE-SEC) The Security track enables you to demonstrate a thorough understanding of ...
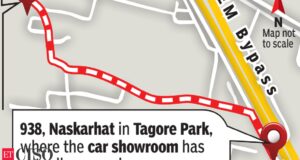
Read More »Kolkata: Hacked e-car showroom map link takes customers for a ride, IT Security News, ET CISO
Kolkata: Hacked e-car showroom map link takes customers for a ride, IT Security News, ET CISO KOLKATA: The city’s first only-electric automobile dealership, which opened on Friday, was short-circuited by a hacker, who has changed the location of the business on Google Map to a narrow lane, around 900m from where the showroom’s actual location off EM Bypass. The showroom ...
Read More » Firewall Training in India Cyber Security Training & Firewall Training Provider in India
Firewall Training in India Cyber Security Training & Firewall Training Provider in India