
Seqrite ( Quick Heal )

Seqrite Unified Threat Management (UTM)
UTM Solution for SOHOs and SMBs
With adoption of sophisticated and complex technology at workplace, SOHOs and SMBs (small and medium businesses) are becoming increasingly vulnerable to cyber threats. It is challenging for network administrators to monitor and prevent potential cyberattacks. They continue to depend on multiple security solutions such as firewall, intrusion prevention systems, antivirus and more, to protect their network security.
In today’s technology-driven world, enterprises have to stay connected anytime and anywhere.
A Unified Threat Management (UTM) reduces security complexities by integrating key IT security features in one integrated network security product.
Seqrite UTM is a high-performance, easy-to-use Unified Threat Management (UTM) solution for small and mid-sized enterprises. The new collaborative platform architecture brings network security, management, backup and recovery of UTM data, and many other critical network services together under a single unified umbrella. UTM is tailored to suit the complexity of emerging threat scenarios. This fully integrated product is a simple and smart way of replacing multiple security programs with one solution.
UTM Product Highlights
» Easy deployment and management.
» Plug-and-play solution without manual intervention or changes.
» Detects and prevents intrusion and protect networks from hackers who can sneak into the system.
» Allows multiple ISPs to be used by UTM.
» Automatically diverts data traffic from inactive ISP to active ISP lines.
» Administrators can control access to applications by configuring rules.
» Provides comprehensive logging and reporting with a user-friendly web-based configuration.
» Easily available customer support and consultation.
Seqrite UTM Features
Networking
» SP Load Balancing
» Policy Based Routing
» Automatic Gateway Failover
» VLAN Support 802.1Q
» Integrated DNS Server
» Dynamic DNS
» DHCP Server
» USB Internet Support 3G/4G
» IP and Port Forwarding
» IEEE 802.1D Transparent Bridging
» Configurable LAN/WAN/DMZ Ports
» NTP Support
» Link Aggregation
» Network Address Translation
(NAT) – Masquerade and SNAT
» Multicast Routing
» H323 and SIP VoIP protocol Support
|
URL Filtering
» Category Based
» Custom Web Lists
» HTTP & HTTPS Blocking
» Time Based Access Limit
» Keyword Blocking in HTTP(S) Traffic
Bandwith management
» User Bandwith control
» Bandwidth Limit for each profile/user
» Group based Bandwith management
User Authentication
» Internal Database
» Active Directory Integration
» LDAP Integration
» IP / MAC Binding
» Multiple Authentication Servers
» Guest User Support
» Group Based Access Control
» Captive Portal
|
|
Administration
» Multiple Administrator Support
» Administrator Profile Management
» Command Line Interface (CLI)
» Multi Lingual Support
» Web Portal Customization
» Backup and Restore Configurations
» Easy Registration (online/offline)
» Device Offline Mode
» Automatic and Manual Update
» Online and Offline Firmware Upgrade
» SNMP support ( V1,V2c & V3)
|
Monitoring & Reporting
» CPU/RAM/Disk Usage
» Alerts (Email and SMS)
» Detailed Reports (Daily, Weekly and Monthly)
» Diagnostic Tools
» Log Viewer
» Port Mirroring
» Syslog support (TCP, UDP and TLS)
» Live user report
» Live and historical usage graph
» Real time web surfing logs
|
|
Mail Protection
» Mail Antivirus and Anti-spam
» (SMTP, POP3 and IMAP)
» Attachment Control
» Keyword Blocking in Email
Firewall & Security Features
» Firewall
» Traffic Logging
» Predefined Firewall Rules
» Zone Support
» Stateful Inspection
» Intrusion Prevention System
» Gateway Antivirus
» Automatic Update for AV, IPS
» DoS and DDoS attack prevention
|
VPN
» IPSec VPN:
• Perfect Forward »Secrecy(PFS)
• NAT Traversal
• VPN Compression
• DNS Setting for PPTP Server
• Multiple Subnet Support
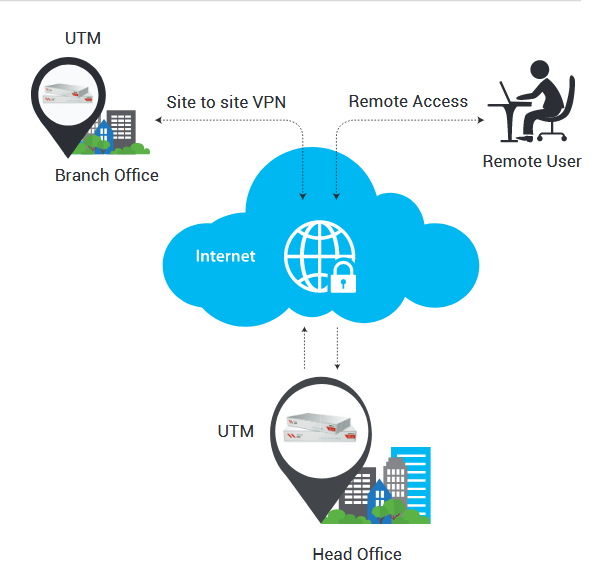
» Site-To-Site VPN
» Remote Access VPN SSL VPN
» Remote Access Client Software
» SSL VPN Compression
» Dead Peer Detection
» Remote and Peer ID
» IPsec VPN failover
|
|
Seqrite UTM Technical Specifications
| Models |
T2S-10 |
T2S-30 |
T2S-60
|
T2M-100 |
2M-250 |
| Interfaces |
|
|
|
|
|
|
Copper GbE ports
|
3 |
4 |
6 |
8 |
10 |
|
Console port
|
1 |
1 |
1 |
1 |
1 |
|
USB Ports
|
2 |
2 |
2 |
2 |
2 |
| Performance |
|
|
|
|
|
|
Firewall TCP Throughput (Mbps)
|
1100 |
1500 |
4100 |
7500 |
10000 |
|
Concurrent Sessions
|
250000 |
500000 |
924000 |
1630000 |
3800000 |
|
New Sessions/Second
|
6050 |
12400 |
26000 |
36000 |
83000 |
|
Antivirus Throughput(Mbps)
|
180 |
200 |
400 |
750 |
1400 |
|
IPSec VPN Throughput(Mbps)
|
620 |
642 |
1153 |
2230 |
6083 |
|
|
90 |
100 |
150 |
250 |
340 |
|
|
480 |
500 |
1650 |
2900 |
6000
|
|
|
160 |
180 |
400 |
750 |
1350
|
|
|
Unrestricted |
Unrestricted |
Unrestricted |
Unrestricted |
Unrestricted
|
|
|
Desktop |
Desktop |
Desktop |
1U |
1U
|
|
|
CE/FCC/BIS
|
CE/FCC/BIS
|
CE/FCC/BIS
|
CE/FCC/BIS
|
|
Seqrite ( Quick Heal ) Firewall Price in India
Just call or email us on
Phone:+91 9582907788
Email: sales@itmonteur.net

 Firewall Training in India Cyber Security Training & Firewall Training Provider in India
Firewall Training in India Cyber Security Training & Firewall Training Provider in India














