Overview
The Data Security Firewall is a leap ahead of the traditional Next Last Generation firewall with Data First Approach for security. It understands organizations data, provides deeper data level visibility and allows to control the data threat surface, taking appropriate security measures to prevent data exploitation.
The Data Security Firewall uses a multi-step process towards Data Security.
The step 1 uses Application Identification Engine that identifies various context point within applications. E.g. the application itself, its Login Id, Sender’s address, Recipients’ address, CC, BCC, Subject, Body Content, attachment, attachment content etc. based on different application.
The step 2 then breaks down the communication packet being sent out using contextual Intelligence Engine to Identify Contextual data within the packet with regards to the application identified and creates a form for the Security policies to act on.
The Step 3 validates various parameters and data security policies on the created contextual data set and check for anomalies over behavior pattern learnt by UEBA and takes suitable actions to prevent data exploitation.
The Step 4 Once validated, the Data Security Firewall records and logs this and creates report.
The Data Security Dashboard is a unique and a powerful At-A-Glance tool for enterprises to have an overview of various Data Threats and overall Data Health of the Organization. It uses the power of GajOS: Bulwark’s granular reporting system and intelligence gathered by Contextual Intelligence Engine to identify various Data Security Policy Violation and generates violation reports for enterprises to take active measures.
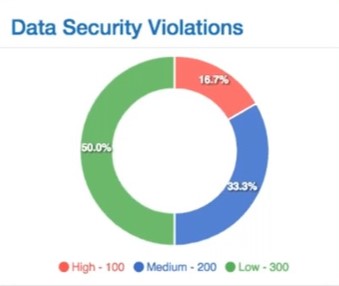
Data Criticality Health Indicator:
Assign Violation Criticality to all your Data Security Policies and monitor the overall Data Security Health based on Criticality Indicators.


Data Security Threat Plane:
Expand your visibility into Understanding and Identifying Each Data Threat vector by their Source for both internal & external communication and control these threats channels effectively.
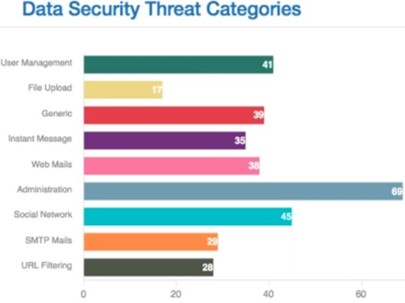
Data Security Threat Categories:
A Multi-Category Threat Identification for a drilled downed data security threat management and deeper understanding of various violations to control them using data security policies.
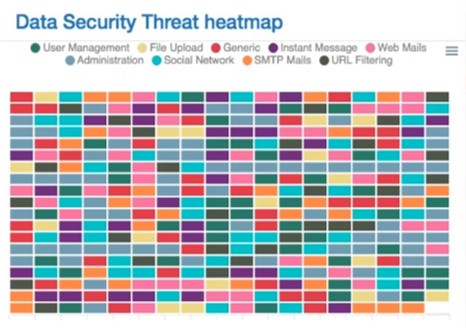
Data Security Threat Heatmap
Understand and identify threat patterns as and when it occurs for an immediate action based on threat categories to identify abnormalities in the organization.
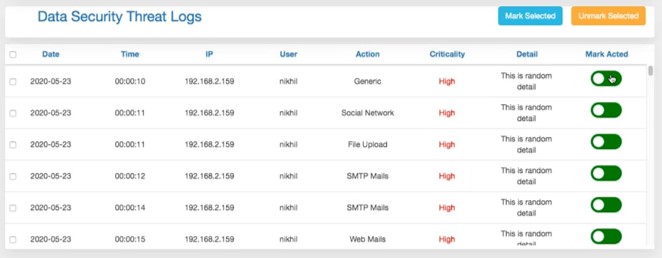
Quick Threat Response
Take Necessary Actions right from the dashboard to protect from threats and improve Data Security Health
Data Security Firewall Platform
The Data Security Firewall is a powerful and robust platform that accommodates various security solutions to help secure data and prevent data exploitation along with better networking functionalities. The Data Security Firewall is powered by GajOS Bulwark and backed by Contextual Intelligence Engine for a deeper data level visibility.
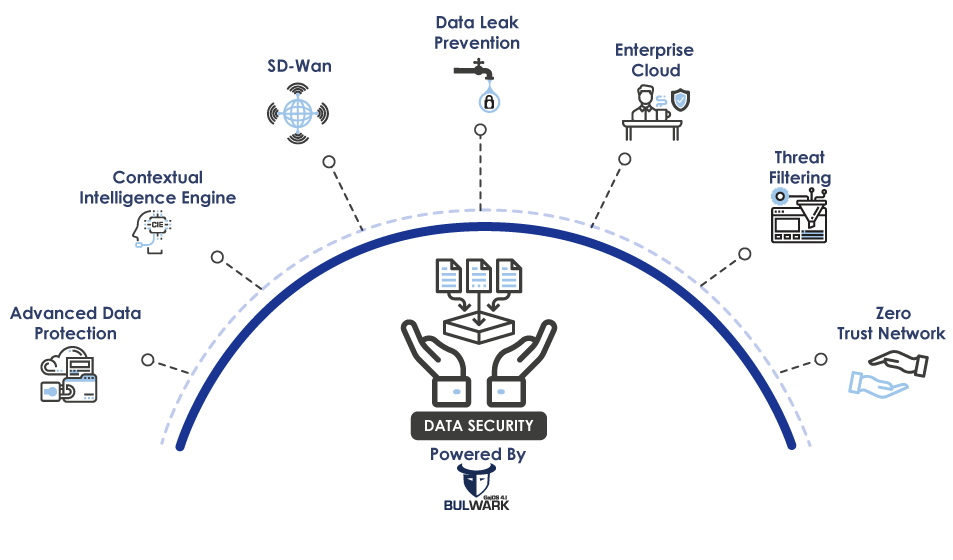
The Advanced Data Protection provides protection from threats involving attempts to unauthorizedly access business critical data using a 2-stage security approach.
Stage 1:
The Advanced Data Protection combined with advanced Machine Learning capability that understands and learns usage pattern and finds outlier to identify suspicious traffic for further process by the security engines to keep them away from the network. The inputs from such a learned pattern is further combined with User Entity Behavior Analyses (UEBA) that creates a pattern of a user and their network activities to identify suspicious activity and alerts the cyber security team of such activities.
Stage 2:
It uses GajShield Threat Labs to keep away malicious and suspicious traffic by identifying signatures and process all unidentified traffic with GajShield’s Intelligent Sandboxing technique that uses Machine Learning & Artificial Intelligence to simulate multiple human actions to trigger and identifies a malicious file in a virtual environment, away from the organization’s network to traps malwares that are injected for stealing data.
Data Security Firewall Benefits
Why Upgrade?
The Data Security Firewall uses a Data First Approach for security. It understands data that the Next Last Generation Firewall did not understand due to its lack of visibility. The Data Security Firewall deep dives into data context and provides visibility unlike any other which helps in preventing data exploitation, covering not only local applications, the Data Security Firewall enforces Data Security Policies across various Cloud and SaaS applications and takes appropriate security measures.
The Data security firewall is self-learning, smart security solution that analysis various data patterns and user behavior to identify anomalies and internal threats. The Data Security Firewall supports Intelligent Packet Filtering.
Data Security Firewall Appliance Features
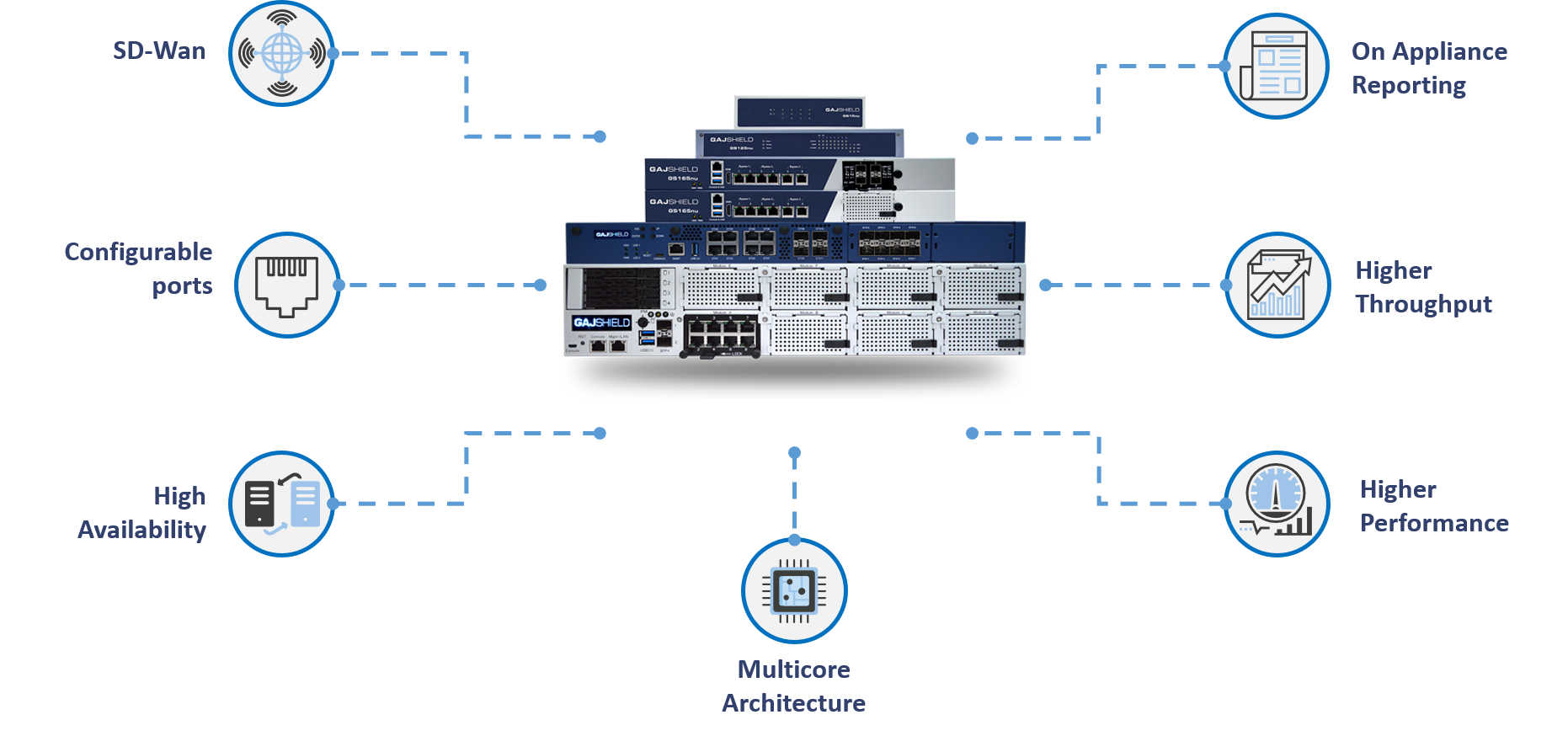
GajShield Data Security Firewall appliances range from GS 20nu to GS 1360nu providing security to SOHO, SME, Large enterprises, Data Centers and more. GajShield firewall appliances deliver the highest levels of performance and security. GajShield’s Data Security Firewall acts as a platform for various essential security solutions for both Data and Network Security. GajShield firewalls are architected to provide high throughputs with multiple solutions deployed and running at the same time. Each GajShield Firewall is evaluated against and has passed ICSA Labs Modular Firewall Product Certification Criteria version 4.1x for general purpose network firewalls, corporate category. Not only does GajShield appliances detect applications independent of port use, it also understands context of data flow with many web-based cloud (SaaS) applications. This empowers an enterprise to inspect data, prevent data leaks and prevent data exploitation. GajShield firewall appliances have industries most powerful Deep Inspection Engine backed by Contextual Intelligence Engine which accurately classifies network application and their contextual data in real time. Each firewall appliance is capable of being configured in Active-Active or Active-Passive High Availability mode. Multiple firewalls can be easily managed using GajShield’s Centralized Management System
 Firewall Training in India Cyber Security Training & Firewall Training Provider in India
Firewall Training in India Cyber Security Training & Firewall Training Provider in India











