Breaking: Bangalore Water Supply Board, Khadi India data leaked on hacker forum

As AIIMS hobbled back to resume regular operations after 19 days of service impact, two more government entities allegedly suffered data breaches in separate incidents.
The Bangalore Water Supply and Sewerage Board (BWSSB) has found a different type of leak to deal with. According to findings by cybersecurity firm Technisanct, a database with over two lakh citizen records belonging to BWSSB was leaked by KelvinSecurity – the threat actor that shot into fame after recent attacks on Vodafone Italy and Chilean banking giant, Banco de Crédito e Inversiones.
On the day prior to the BWSSB incident, a threat actor, LeakBase, dumped the stolen database of the official e-commerce website of Khadi India on popular hacker forum, Breached.vc. LeakBase is the hacker group that leaked 1.6 crore user records from the government-operated Swachhata platform in September this year. The National Informatics Centre is the domain name registrar of both websites.
Reports shared exclusively with ETCISO shows that both leaked databases contain personal information of customers.
The Khadi India leak, although affecting far fewer customers (13,112), contains PII, user IDs, payment details, order history, and verification codes, among others.
A BWSSB spokesperson, Sudhir, tells ETCISO that the organization has not faced a data breach and that they haven’t received any communication that points towards a ransomware attack. Khadi India is yet to respond to our queries on the alleged data breach.
The story will be updated with the latest developments on both incidents and the organizations’ response, should anything come through.
Bangalore water supply board has a leak
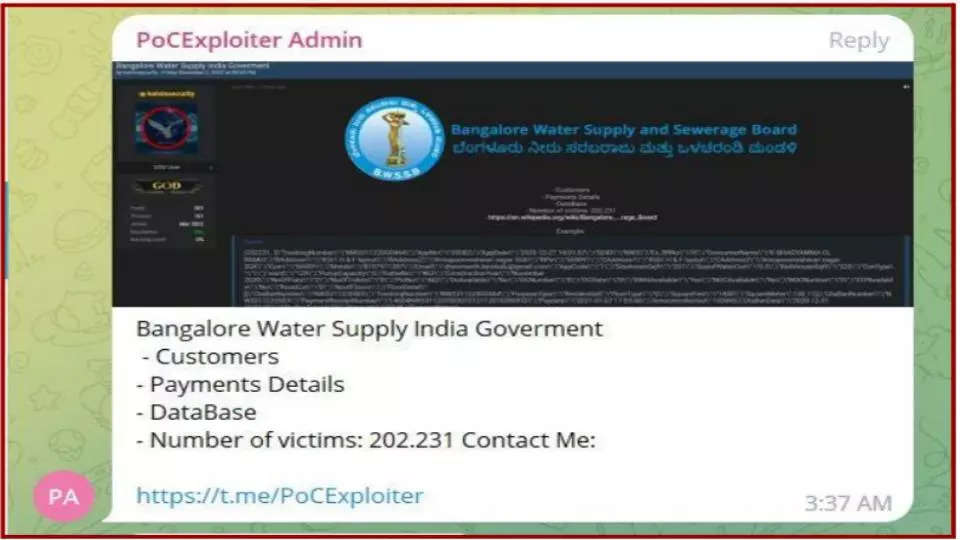
Technisanct researchers tell us that the BWSSB leak affects 2,02,231 citizens whose residential information – building details including ‘khata’ number, floor details, square feet and built up area, pump capacity, etcetera. Victims’ contact information and payment details have also been compromised.
Information about the victims’ water supply connection and meter details such as meter type, make, and water consumption is included in the leaked data.
According to Nandakishore Harikumar, CEO of Technisanct, the BWSSB leak is a clear example of government entities not securing customer data. “Our proposed personal data protection bill has not got proper framework on bringing government entities into regulation,” he says.
Khadi India leak smaller, but just as concerning
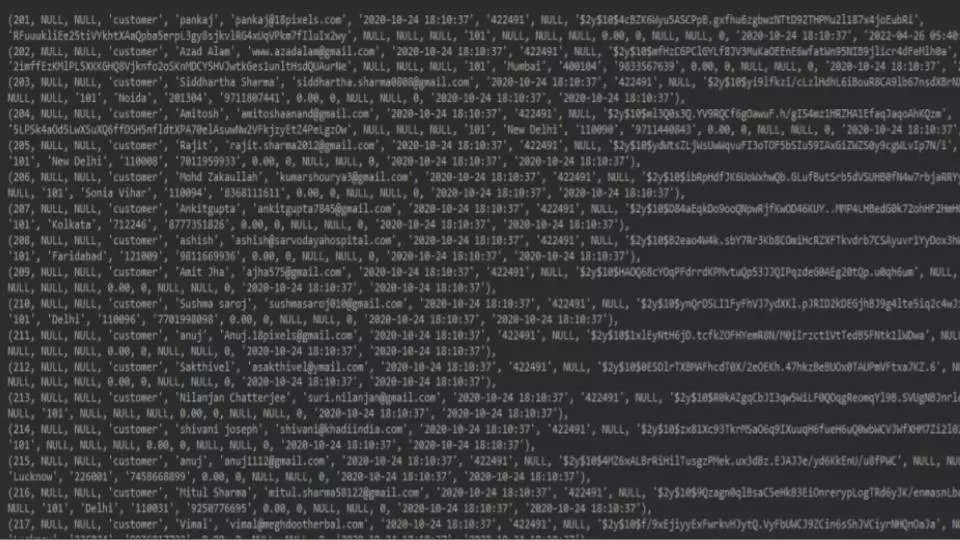
Even though the number of affected parties are fewer in comparison to BWSSB’s 2L+ leaked records – just over 13,000, Harikumar warns that there is a huge possibility of victims getting scammed.
“The breach has several pieces of information with which the scammers could trick consumers into multiple scams. There are various debit/credit card data available. Even though it’s masked, it can pose a huge threat,” he explains.

Harikumar underlines that customers should be alerted about the dangers and be instructed to block their registered payment cards.
In its previous exploit on the Swacch City platform, CloudSEK researchers had found that LeakBase operators had leaked usernames, emails, passwords, mobile numbers, OTP-related info, login IPs, and individual user tokens on the same hacker forum, Breached.vc.
LeakBase is back after a long hiatus – the group shut shop in 2017 after the feds had closed in, according to Israeli cybersecurity company KELA’s report.
The company’s researchers say that LeakBase shares hundreds of new SQL databases of companies from around the world. The hacker group has thus far leaked 50 databases on Breached.vc.
 Firewall Training in India Cyber Security Training & Firewall Training Provider in India
Firewall Training in India Cyber Security Training & Firewall Training Provider in India











