VPN Service Provider in India

VPN,VPN India,VPN Services,VPN Company,VPN Services India VPN, VPN Service, VPN Services Provider Company India, Virtual Private Network ( VPN ) VPN Service Provider in India, VPN, VPN India, VPN Services,VPN Company
VPN Service Provider in India
Firewall Firm, a VPN Service provider company in India, providing VPN Services on Firewall and providing support 24×7 for work remotely. A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g., a laptop, desktop, smartphone, across a VPN may therefore benefit from the functionality, security, and management of the private network. Encryption is a common, though not an inherent, part of a VPN connection.
VPN technology was developed to allow remote users and branch offices to access corporate applications and resources. To ensure security, the private network connection is established using an encrypted layered tunneling protocol, and VPN users use authentication methods, including passwords or certificates, to gain access to the VPN.
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely.
In other applications, calling a proxy a VPN is a marketing technique on the part of consumer VPNs. Internet users may secure their connections with a VPN to circumvent geo-restrictions and censorship or to connect to proxy servers to protect personal identity and location to stay anonymous on the Internet. Some websites, however, block access to known VPN technology to prevent the circumvention of their geo-restrictions, and many VPN providers have been developing strategies to get around these roadblocks.
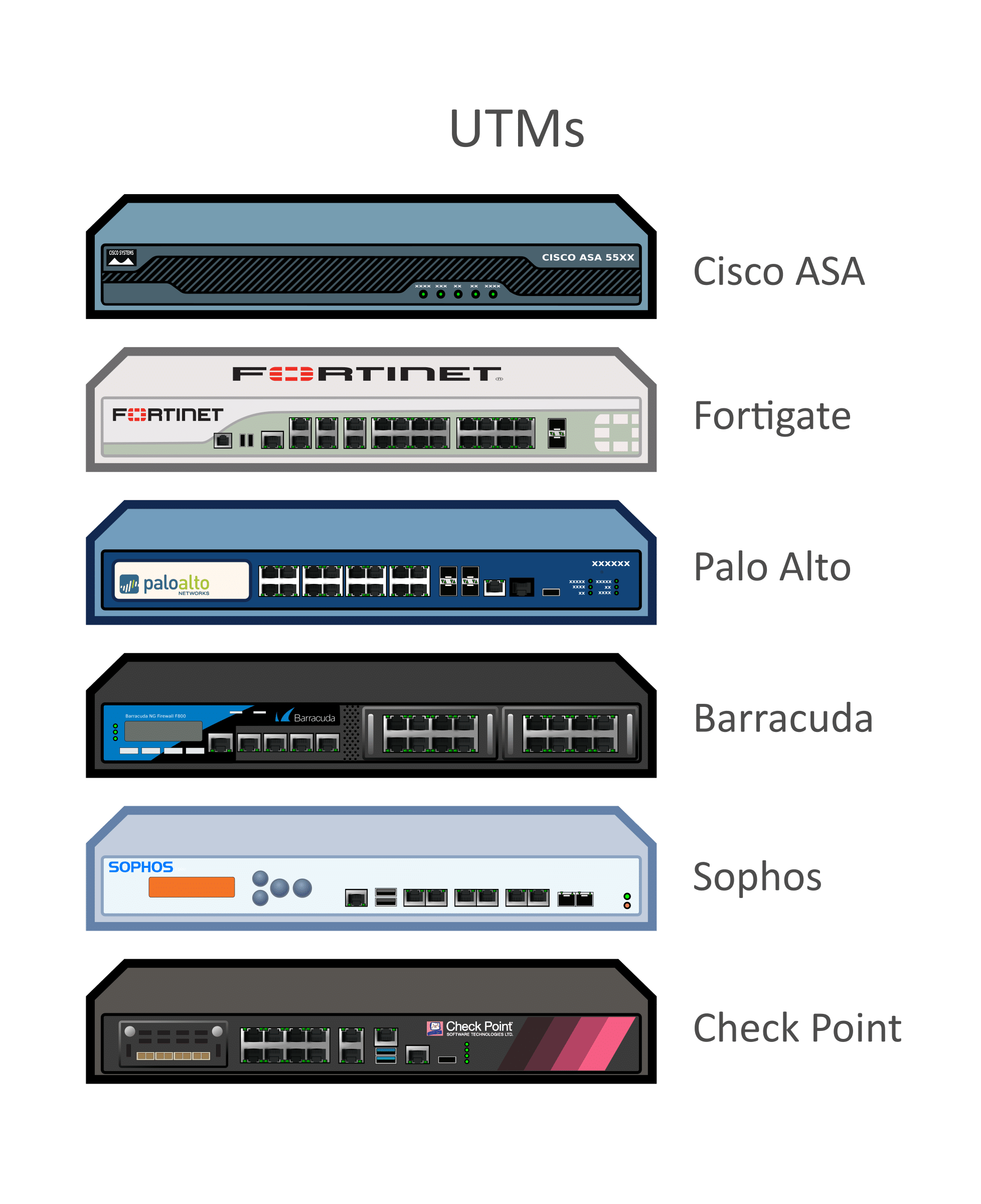
Enterprise Infrastructure VPNs
| Ratings | |||
 AnyConnect VPN by Cisco |
|||
AnyConnectby Cisco |
4.5 | ||
| “Cisco VPN is guenue and user-freindly software with less complex while establishment.” | |||
 FortiClient VPN by Fortinet |
|||
FortiClientby Fortinet |
4.4 | ||
| “Forticlient easy to install but muti function, Endpoint antivirus and VPN function too.” | |||
 Mobile VPN by Pulse Secure |
|||
Mobile VPNby Pulse Secure |
|||
| “The most important shield for your device” | |||
 Citrix
|
|||
| Citrix Gateway (formerly NetScaler VPN, NetScaler Gateway or NetScaler Unified Gateway) by Citrix |
|||
| “”Single url remote access and Secure interface.”” | |||
 Cloud VPN by Google |
|||
Cloud VPNby Google |
|||
| A Cloud VPN is a cloud-based network infrastructure that delivers VPN services. | |||
 GlobalProtect VPN by Palo Alto Networks |
|||
GlobalProtectby Palo Alto Networks |
|||
| “Palo Alto GlobalProtect is a great option for a VPN client on Mac and PC” | |||
 Secure TLS VPN by Pulse Secure |
|||
Secure TLSby Pulse Secure |
|||
| “Very flexible product that can solve all our connectivity problems” | |||
 Mobile VPN with SSL by WatchGuard
|
|||
Mobile VPN with SSLby WatchGuard |
|||
|
“Mobile VPN with SSL: Perfect VPN tool for connecting from differnet locations.”
|
|||
 IKEv2 VPN by Apple |
|||
IKEv2by Apple |
|||
| “Supremely Useful VPN Configuration Tool” | |||
 Check Point Capsule VPN by Check Point Software Technologies
|
|||
Check Point Capsuleby Check Point Software Technologies |
|||
|
“Checkpoint capsule for OOB”
|
VPN (Virtual Private Network) Service providers in Delhi NCR India
Work from Home Securely: Enterprise
Is your remote workforce expanding beyond your current mobile access or VPN solution? Deploy VPN Services to concurrently and safely connect remote employees and devices.
 Firewall Training in India Cyber Security Training & Firewall Training Provider in India
Firewall Training in India Cyber Security Training & Firewall Training Provider in India





 Form Factor – Desktop
Form Factor – Desktop










